Hackfest 2016 - Infinity Edition Summary

On the first weekend of November, I had the chance to attend Hackfest in Quebec City, the largest hacking and InfoSec event in Canada! Here is a summary of the 2 awesome days, and nights, I had there.
First of all, I must say that it was the 8th edition of the event, thus the Infinity tagline, and the organizers got everything under control. The venue was very well organized, the speakers were professionals and the CTF were fun and challenging, mostly challenging in fact. Even though it was my second year attending the event, I’m not an InfoSec guy. I’m a developer who wants to do a better job at keeping its apps’ data safe. This brings me to the point that Hackfest, and InfoSec in general, is a very inclusive community. I could discuss with people from Quebec City, Toronto or USA working at different places such as antivirus company, consulting firms, HP or even freelancing.
Day 1
On the first day of conferences, I attended different talks on various subjects such as HTTP/2 weaknesses to DDoS attacks, how France is protecting the country against cyberterrorism, best practices regarding server configuration(basically: tighten permissions + only run the services you need/use), how bitcoins is not as anonymous as we might think.
After lunch, I attended a less technical talk on the psychology of the hacker persona. How individuals with that mindset tend to suffer from stress and even depression because they feel ignored and powerless within their organization.
Also, there was a presentation of the Burp plugin BurpSmartBuster to quickly scan files and directories of a specific URL. This tool is interesting but I realized that I really need to look more into Burp Suite before the next CTF or if I want to get into bug bounty.
Finally, a very interesting talk on how some prisons protect themselves from drones breaching their perimeter. They process audio and images coming from a device equipped with cameras and mics sensors to detect and identify drones. They can then track them and notify the prison’s officers to lock down prisoners and seek for the operator of the drone to take it down. I was surprised to learn that they can’t simply shoot the drone down. They must find, then restrain, the operator or use nets to catch the drone without breaking it. Otherwise, they are liable for damage done to others’ property.
Workshop with Peter Yaworski - Getting Beyond Bug Bounty Nood Status
During the evening, Peter Yaworski was giving a workshop on getting started in bug bounty. It was really interesting and I could relate to his experience because he has a developer background turning into bug bounty.
Peter got started about a year ago in bug bounty and he documented everything he learned along the way in his book Web Hacking 101. His book is clearly a great resource for someone starting out in bug bounty. I had the chance to spend some time with Peter during the OWASP mini-CTF and he would explain to me the vulnerabilities by referring to his book. I almost bought his book right away(which I will probably do this summer when I have time to play around with infosec stuff)!
The workshop began with an explanation of what bug bounty is. Then, where to find bug bounty programs. Big companies like Google or Facebook have their own programs, but platforms like HackerOne or BugCrowd allow smaller companies to post bounty offers publicly or privately(invite only).
Here is a summary of the lessons learned by Peter during his first year in bug bounty:
- Hacking is not easy money
- Don’t give up!
- When submitting a bug report, also provide a proof of concept to prove there really is a bug
- Your reputation is gold on the bug bounties platforms
- Hacking skills are needed to succeed, but observation and relationships are equally important
- Read the documentation to find what might have been overlooked by others
- When you start out, you will learn a lot from others. So, when the time comes, give back and share your knowledge
- There is not much focus on mobile yet, explore less exploited technologies
- Make sure to understand correctly the scope provided with the bounty offer
- Better reports => Better relationships => Better bounties
He also provided a list of tools to get started:
- burp
- fiddler proxy
- nmap
- gitrob
- sublist3r
- reconengineer
- wappalyser
- xsshunter
- dex2jar
To learn more about Peter’s work, his podcast, YouTube channel and much more, you can go to his website.
Hackfest CTF

On the first evening of the event, a huge CTF is organized so you can test your ability to hack software, exploit vulnerabilities and even try to solve some hardware/electronics challenges.
Usually, people go there in teams of 4, but we were only 2 so the challenge was even greater. We didn’t perform very well but we had a great time and learned a lot to be better next year! The atmosphere was pretty nice, there was good music and seeing all these people working hard at the same time in the room to solve the puzzles was very motivating. I can’t wait for next year to give it another shot!
Day 2
On the second day of the conference, I started with a talk about race conditions in web applications. It was interesting from a developer standpoint because concurrency problems might be easily overlooked when developing and they are pretty hard to reproduce. The speaker presented a tool he is working on to test for such race conditions in web apps: race-the-web. He also suggested a book on web apps security: Web Application Hacker’s Handbook, written by the guy who created Burp listed above.
The next talk was about using Java serialization as an attack vector to abuse file I/O, network I/O and eventually create DDoS by memory or process overflow. A good reminder on making sure to sanitize input before trying to serialize it(well, before doing pretty much anything too…). After that, I attended a lighter talk on ships hacking. It was more about social engineering and how cruise ship organizations can be manipulated in order to gain privileges while cruising or rebates when scheduling a trip.
Following lunch, I attended a talk about the Dark Web economy featuring the one and only Johnny Xmas. It was a very entertaining talk, as you would expect from Johnny. The presentation exposed some myths about the Dark Web such as the presence of hitmen seeking for jobs(which there are not any, in fact). They also warned us about the tremendous amount of scammers trying to rip you off by selling junk or fake stuff. Also, if you ever decide to visit the darkness of the web you must be careful because the authorities are playing double agent to catch illicit transactions.
Then, there was a talk about game hacking for fun rather than profit. It mostly explained how you can tamper with data in RAM to modify the game’s state and/or behaviour. Thereafter, a speaker compared the preparation of the defense security team to the training of fighter pilots. Their rigorous drills and practice prepare them for the worst situation, whether offensive or defensive. We should do the exact same thing with the security defense team. Invest as much in building a strong defense as in actively testing your system with an offense team.
Finally, the last talk I attended was about iOS security. It was pretty high-level, but interesting nonetheless. We must be careful when integrating third party libraries in our code because we might integrate their vulnerabilities at the same time. We must be careful when using webviews because there is a function to evaluate arbitrary Javascript, so user input must be sanitized before going through. We should also be cautious when the app goes in background, because the OS is taking a snapshot which might disclose sensitive data in the app-switching view. We can get notified on entering background and update our UI to hide that data.
La French Connection Podcast
On the second night of the event, the organizer of the conference started a new podcast, La French Connection, about security tips and news. They recorded the first episode at Hackfest in front of a small audience, mainly because the ESET party was happening in another room. It was a good show, the host and its guests were funny and got along very well.
ESET Party and OWASP mini-CTF
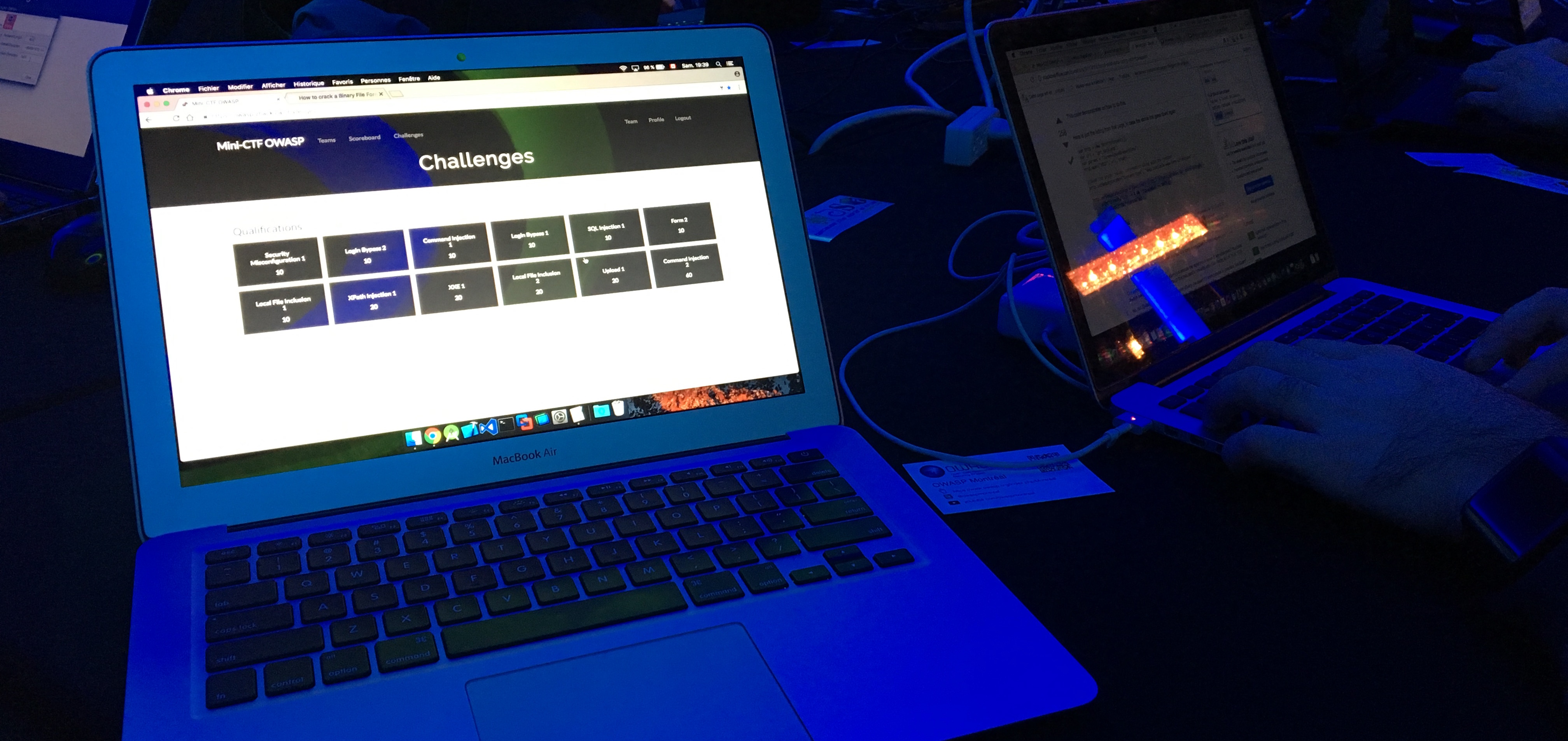
To celebrate those amazing days of talks, learning, sharing and socializing, ESET was sponsoring a nice party. Right at the door, we got goodies/swag and a ticket for a free drink so it already was a pretty nice event. Ambiance was great and there was hacking and lock picking challenges. We decided to try the OWASP mini-CTF and had a lot of fun(we even managed to solve some challenges!).
Wrap up
I definitely had an awesome time at Hackfest! I will make sure to share what I learned and try to contribute to the InfoSec community during the coming year.
Until next year, Hackfest! :)
Any comments? Hit me up @codingjames